As soon as one sets off their journey on the Instagram platform, getting more and more followers is the first thing they often run after.
Following the hiding of like counts on Instagram posts, a user’s followers count has become a prominent aspect for influencers to show their worth to the advertising companies.
Engagements and other insight also play a vital role, but it is the number of Instagram followers that comes into consideration whenever a company wants to approach an influencer or celebrity.
And when it comes to “Instagram Followers”…
Some resort to apps, while the rest try out paid services.
However…
Something that recently happened with the users of ‘Social Captain’ aired a layer of tension among Instagram users who opt-in for the services.
What is Social Captain?
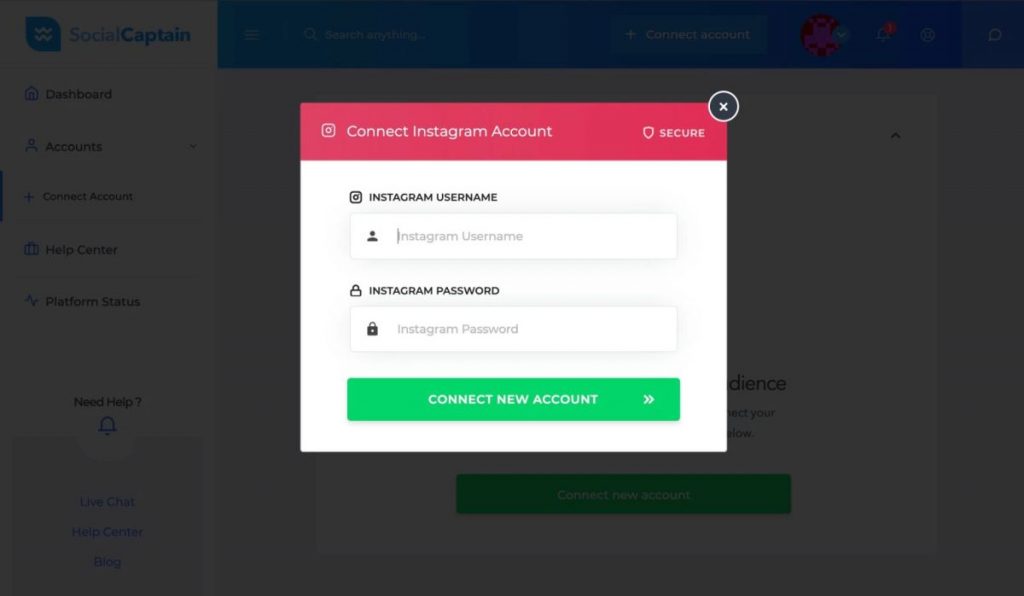
Social Captain is an online start-up that boosts a user’s Instagram profile by serving them organic followers and likes.
I mean,…that is what site claims.
I just checked it out and everything seemed fine with the website.
But…
It’s NOT TRUE on “TECHNICAL AND SECURITY” grounds.
The app was recently found to have exposed thousands of user passwords and usernames.
Likewise most of the apps claiming to provide followers, Social Captain too asked users to connect their Instagram account with the platform.
Every user who starts at the platform had to enter their credentials to get started and use the service.
However…
It was TechCrunch (an American Media Company) first who brought it to light that the app was storing the passwords and username of users in unencrypted plaintext.
Any user who viewed the source code of the page could easily see the credentials in the plain text following they connect their Instagram account with the service.
Moreover, the most shocking fault that surfaced soon after was an app bug that was compromising the security of thousands of Instagram accounts.
The bug made it possible for anyone out there to access any Social Captain user’s profile without even having to log in or create an account on the website.
Anyone could simply enter a user’s unique account ID into the company’s web address and they could grant access to their Social Captain account.
And ultimately, to their Instagram details (password, username, email, etc.)
Moreover, since the user account ids were mostly sequential, anyone could easily access any user’s profile by viewing their username and password.
A security researcher who preferred not to be named alerted TechCrunch to the vulnerability and provided a spreadsheet of about 10,000 scraped user accounts.
The records contained 4700 sets of Instagram passwords with their usernames, while for the rest of the record contained user email ids and usernames.
The scraped data also showed that 70% of the accounts were paid members, while the rest used the service free version.
As of now, Social Captain has confirmed that it had fixed the vulnerability by preventing direct access to other users’ profiles.
However, the password and the other account info is still viewable in the source code of the web page.
“Early analysis indicates that the issue was introduced during the past weeks when the endpoint, meant to facilitate integration with a third-party email service, has been temporarily made accessible without token-based authentication,” said Anthony Rogers, chief executive at Social Captain.
“As soon as we finalize the internal investigation we will be alerting users that could have been affected in the event of a breach and prompt them to update the associated username and password combinations,” he said.
Roger; however, did not mention how long would it take to carry the entire investigation.
It is currently advisable for users who signed up for the service to change their passwords as soon as possible.
An Instagram spokesperson said, “We are investigating and will take appropriate action. We strongly encourage people to never give their passwords to someone they don’t know or trust.”
As per Adam Brown, the Manager of Security Solutions, at Synopsys Software Integrity Group– the design flaws are one of the main causes of approximately 50% of all software vulnerabilities.
“They are seldom detected without performing a design review as this activity requires select expertise. That said, in this case, a penetration test should have easily identified this flaw,” Brown told IANS.
“This is especially bad for affected users not just because their Instagram passwords are now breached, but also due to the fact that people commonly reuse passwords which could lead to unauthorized access of additional accounts by extension,” he elaborated.
By the way, if you are thinking of opting for paid services, make sure you research well about the service and read all terms and conditions before entering your private credential in any third-party apps or service.
Drop down your queries in the comments below and please do share if you liked this article.
P.S.- If you want to read more posts like this, subscribe to our newsletter so you never miss any update.
Till then?
See you next time!
Bye-bye!
