Laxman Muthiyah, a Chennai-based security analyst, earned a reward of USD 30K as a participant in a bug bounty program.
Shortly after he detected a glitch inside app’s (Instagram) code, Mr Muthiyah mentioned the susceptibility in code that made it possible for him to hack pretty much any Instagram profile.
He found out that it was quite feasible to take control of anyone’s Instagram account by merely prompting a password reset, calling for a recovery code, and experiment with the likely recovery codes across the security shield.
Laxman reported the vulnerability to the Facebook security team right away; he observed the flaw.
Fb team, although was unable to reproduce it initially due to lack of information in Muthiyah’s report.
However, after a few e-mails and proof of concept video, Muthiyah convinced the FB team that the attack is feasible.
Following confirmation, Facebook and Instagram security staffs addressed the concern and also honoured him $30,000.
How Bug Compromised User Security ?
To prove, Muthiyah explains that as soon as a person inputs his phone number, they are going to be delivered a six-digit passcode on their cellphone.
They need to type in the code so as to alter their security password.
For this reason, assuming that we manage to try out every possible one million code on verification endpoint, one is equipped with the power to alter the security password of virtually any Instagram account.
Nevertheless, Muthiyah was quite sure that there should be some rate restrictions against these kinds of brute force attacks. To that end, his evaluations did prove the existence of rate-limiting.
He sent out about a thousand requests, 250 of which passed through.
While the rest 750 requests were rate limited!
He then tried out yet another thousand request, but this time a number of them got rate limited.
Therefore, their programs are certainly legitimizing and rate-limiting the requests effectively.
Their systems are validating and rate-limiting the requests correctly.
The number of requests plus the lack in reference to blacklisting was a couple of factors that dawned on his mind.
Muthiyah was capable of sending requests constantly without getting impeded.
That too, despite the fact when the quantity of requests he sent out within a segment of the time was controlled.
Following a couple of times of constant examining, Muthiyah identified two points that enabled him to get away from their rate-limiting execution.
- Race Hazard
- IP rotation
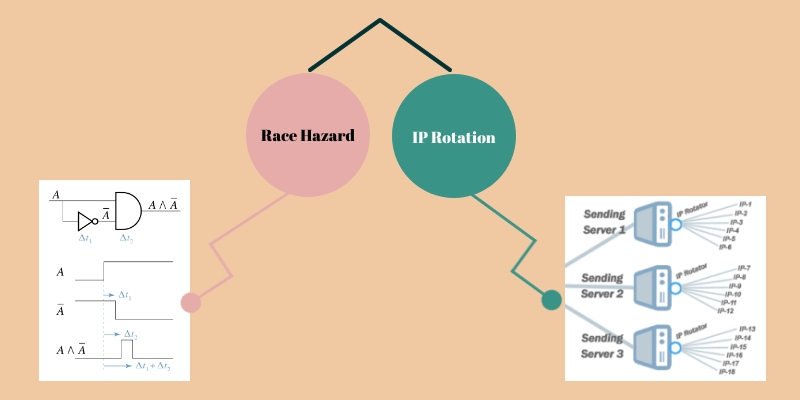
Factors that Made it Possible!
Sending out simultaneous requests employing a number of IPs made it possible for him to send a lot of requests without any restrictions.
The amount of requests one sends usually hinges on concurrency of requests plus the total number of IPs employed.
At the same time, I recognized that the code runs out within 10 mins, which makes the attack even more challenging.
For these reasons, he said that one needs to have thousands of IPs to execute the attack.
He disclosed the vulnerability to Facebook’s security crew.
At first, the company was not able to reproduce it because of the inadequacy of details in Muthiyah’s report.
However, following a couple of e-mails and strong evidence of practical video, he was able to convince the security crew that the attack was plausible.
Nonetheless, Paul Ducklin, a Senior Technologist at cybersecurity major Sophos, cautioned users at the same time about the vulnerability spotted by Muthiyah.
He further adds that people must acquaint themselves with the procedure related to acquiring back control of their accounts, just in case user gets hacked.
“In case any of your accounts do get taken over, familiarise yourself with the process you’d follow to win them back. In particular, if there are documents or usage history that might help your case, get them ready before you get hacked, not afterwards,” Ducklin said in a statement.
This is not the first moment when Muthiyah uncovered a flaw within an app.
Earlier, he exposed a data expunging and a data disclosure bug on Facebook.
The first flaw zapped almost all photographs without knowing a user’s security password.
On the other hand, the second glitch misled users into installing an innocent-looking cell phone application that can go over all Facebook images without being granted the accessibility to the user account.
Lemme know about your thoughts in the comments section below!
See you next time!
Bye-bye
